Making Security Simple
Somewhere in the world right now there is a very happy hacker.
He is happy because he just managed to get into a small-time laptop on some outpost network in the middle of nowhere.
Why Take Chances?
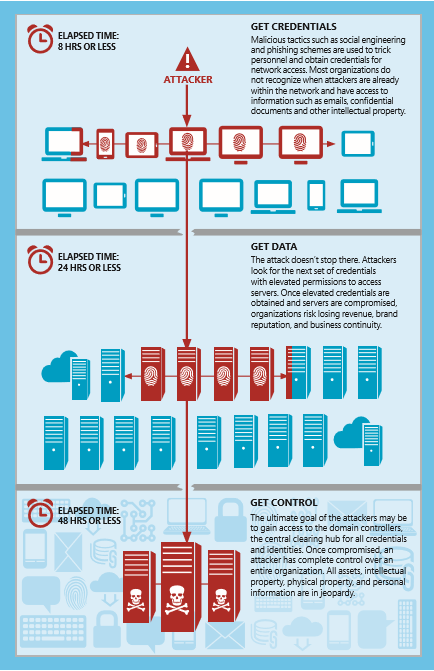
You might wonder why he is so elated… Well, the outpost is a part of the enterprise network of a household name company, and this particular computer has the hash for the administrator credentials. You see, this particular happy fellow has been going from one workstation to the next in hopes of finding the digital footprints that will give him full administration of the network. He has found it, and now he will wait for the right time because well… you don’t know he’s there, do you?
Its called Pass the Hash(PtH), it is a form of credential theft, and it’s not just one hacker, its armies of them, sometimes working for rogue states attempting to gain access anywhere they can. They are legion.
Halcyon has done battle with them and learned all about their digital footprints. We have developed a set of defenses to keep your company safe from happy hackers the world over. We specialize in custom solutions and also Microsoft recommended deployments of Active Directory to eliminate the Pass the Hash vulnerability. We can deploy a change awareness solution that will prevent or alert you to any change in your environment. We can let you know who is trying to, and even failing to add themselves to specific groups or resources in your security structures.
At Halcyon, we believe in security from the ground up. Keeping things uniform is critical to securing your enterprise. A solid Identity Access and Governance Strategy keeps you inoculated from the moment it is implemented.
The only way to protect your company from credential theft and corporate sabotage from within is to always Assume a Breach, and act before you are forced to. Let us help you get there.

Somewhere in the world right now there is a very happy hacker.
He is happy because he just managed to get into a small-time laptop on some outpost network in the middle of nowhere.
You might wonder why he is so elated… Well, the outpost is a part of the enterprise network of a household name company, and this particular computer has the hash for the administrator credentials. You see, this particular happy fellow has been going from one workstation to the next in hopes of finding the digital footprints that will give him full administration of the network. He has found it, and now he will wait for the right time because well… you don’t know he’s there, do you?
Its called Pass the Hash(PtH), it is a form of credential theft, and it’s not just one hacker, its armies of them, sometimes working for rogue states attempting to gain access anywhere they can. They are legion.
Halcyon has done battle with them and learned all about their digital footprints. We have developed a set of defenses to keep your company safe from happy hackers the world over. We specialize in custom solutions and also Microsoft recommended deployments of Active Directory to eliminate the Pass the Hash vulnerability. We can deploy a change awareness solution that will prevent or alert you to any change in your environment. We can let you know who is trying to, and even failing to add themselves to specific groups or resources in your security structures.
At Halcyon, we believe in security from the ground up. Keeping things uniform is critical to securing your enterprise. A solid Identity Access and Governance Strategy keeps you inoculated from the moment it is implemented.
The only way to protect your company from credential theft and corporate sabotage from within is to always Assume a Breach, and act before you are forced to. Let us help you get there.