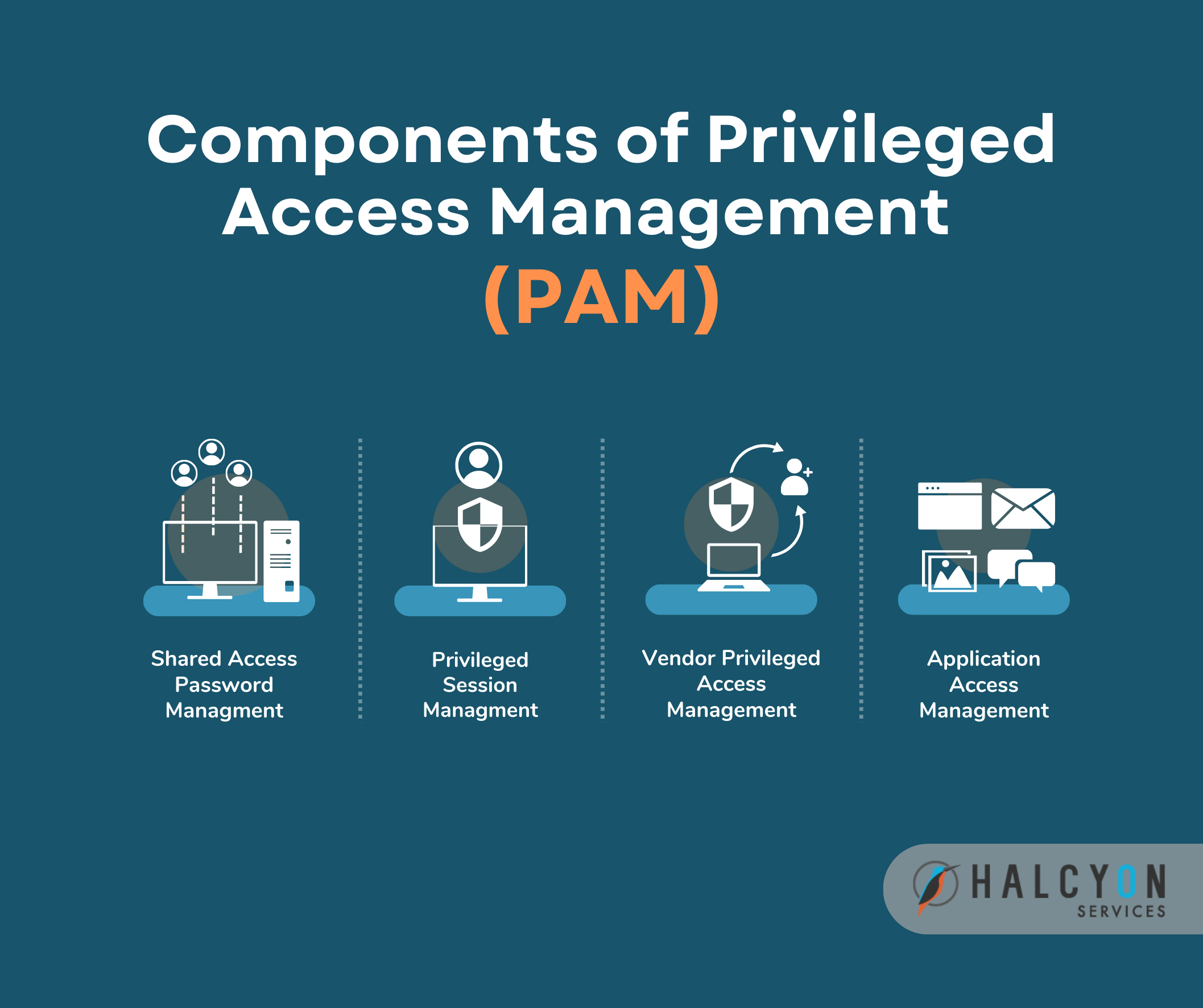
Strengthen Your Privileged Access Management: 4 Key Components of Privileged Access Management
Cindy Morrison2023-09-13T16:15:36+00:00Businesses today face increasing security threats to privileged user accounts that can access applications and infrastructure. Privileged Access Management (PAM), has become a crucial cybersecurity strategy to ensure [...]