Our Latest Insights
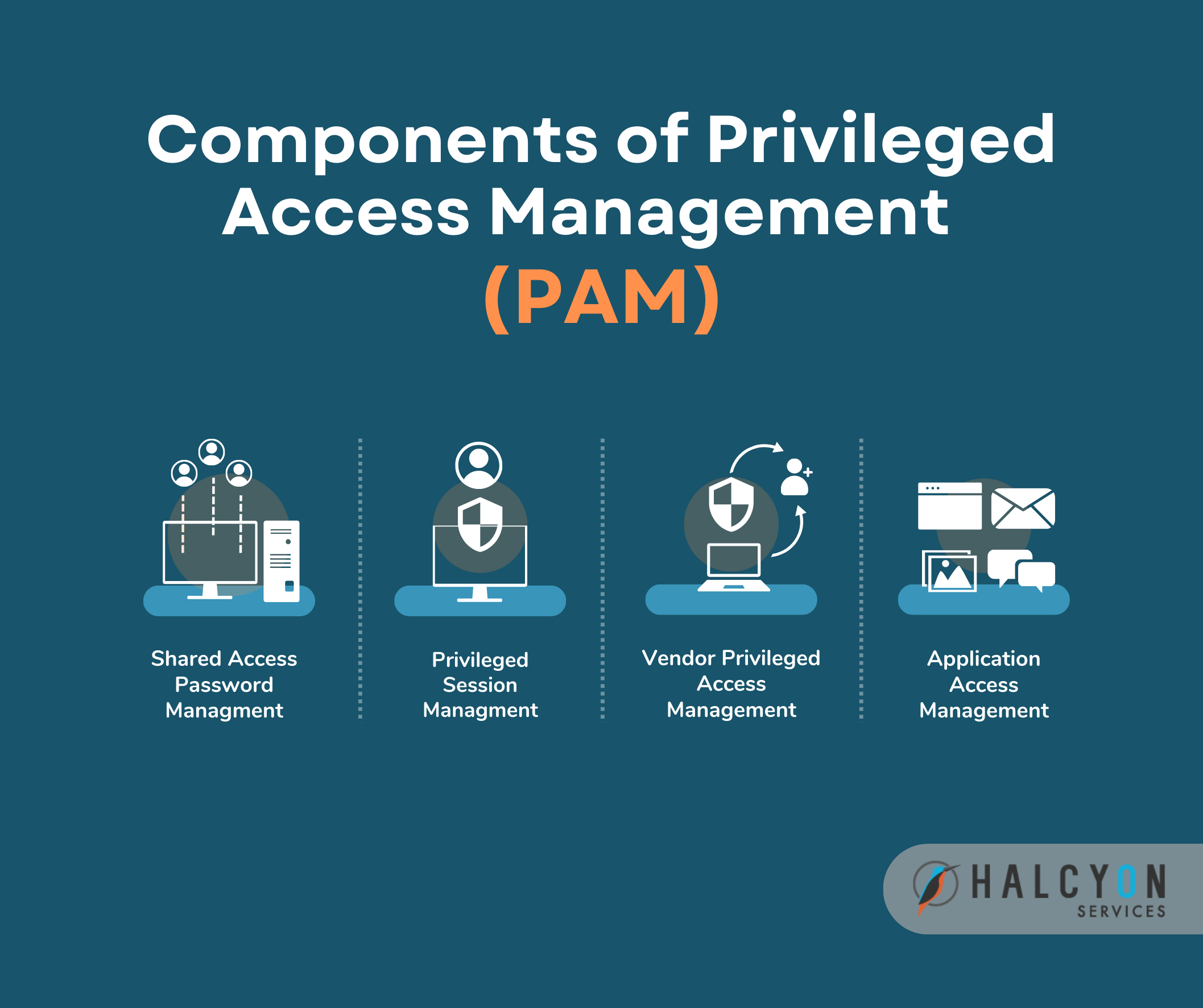
Strengthen Your Privileged Access Management: 4 Key Components of Privileged Access Management
Businesses today face increasing security threats to privileged user accounts that can access applications and infrastructure. Privileged Access Management (PAM), has become a crucial [...]
Article: Making Zero Trust Real (One Identity Whitepaper)
Let's Work Together! Let's Work Together!
Article: Making Zero Trust Real (One Identity Whitepaper)
Let's Work Together! Let's Work Together!
Tackling Insider Threat Detection With User Behaviour Analytics
A great read from Quest explaining how to spot activities that pose true risk, without getting buried in an avalanche of alerts, using Quest's Change Auditor Software. This is something that Halcyon is particularly skilled at.
Spotlight : Azure Site Recovery
Businesses revolve around data and the availability of data. Downtime is no longer an acceptable risk for any industry. Sound planning around BC/DR (Business Continuity and Disaster Recovery) is fundamental. Traditionally, businesses have looked at DR to require a near mirror of their production environment. This is a costly and difficult situation to justify.
Spotlight : Azure Site Recovery
Businesses revolve around data and the availability of data. Downtime is no longer an acceptable risk for any industry. Sound planning around BC/DR (Business Continuity and Disaster Recovery) is fundamental. Traditionally, businesses have looked at DR to require a near mirror of their production environment. This is a costly and difficult situation to justify.
Spend Less Time Managing Roles
Companies evolve. People come and people go. Roles change. This is a fact of life that can translate into thousands of hours of work for the people who are responsible for managing the infrastructure. Even in smaller companies, it can be a daunting task considering the number of applications staff need to access on a daily basis.